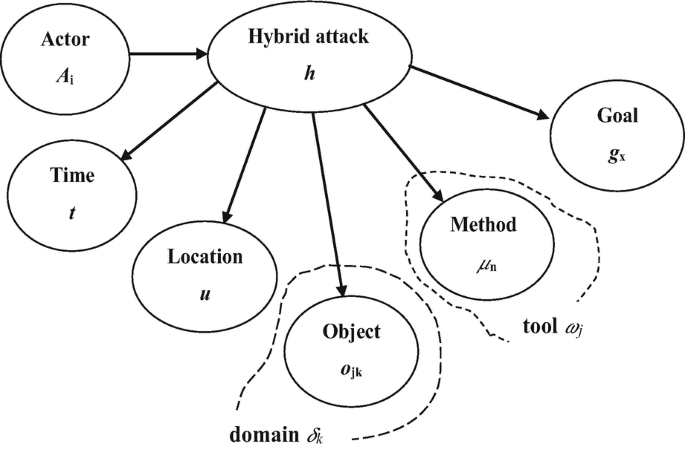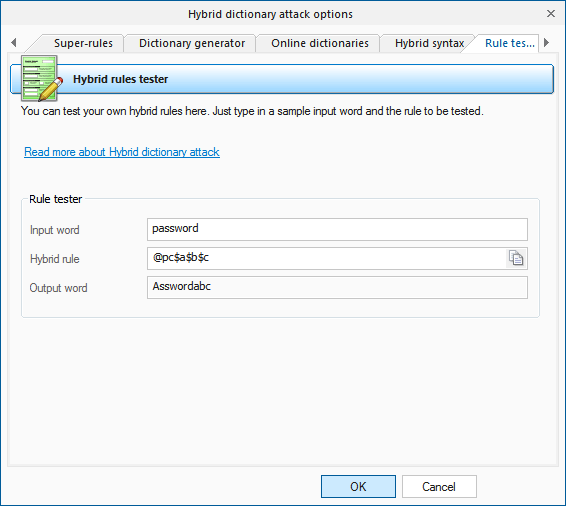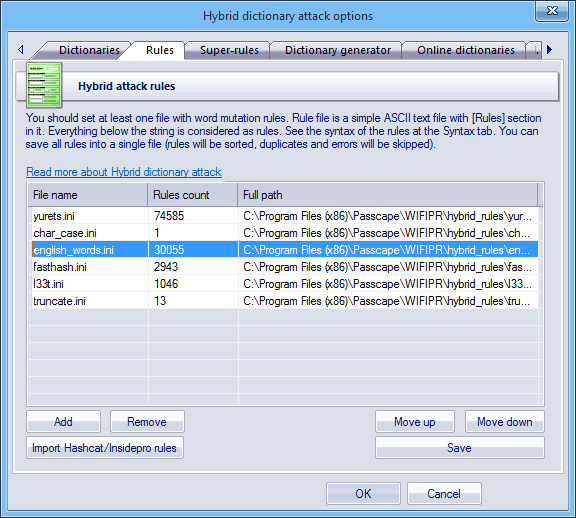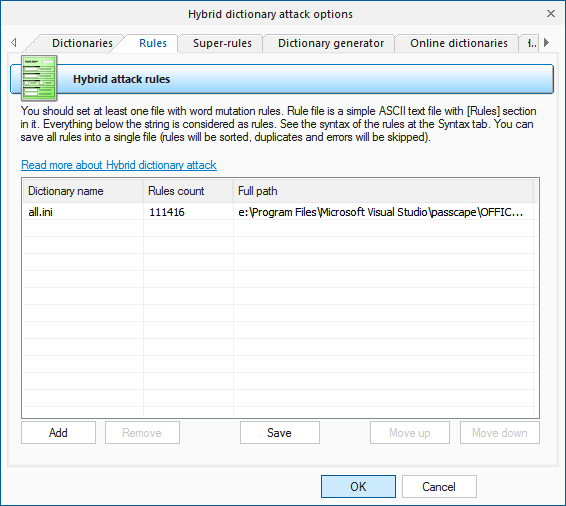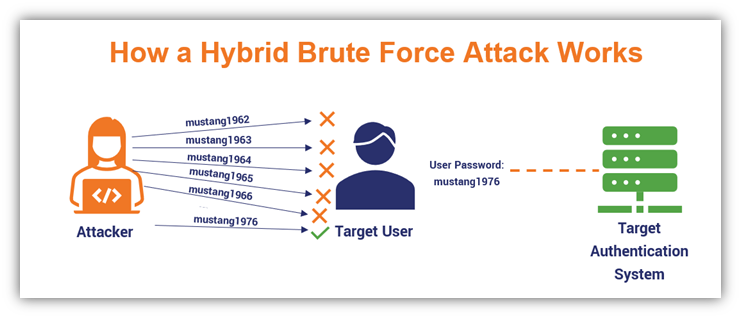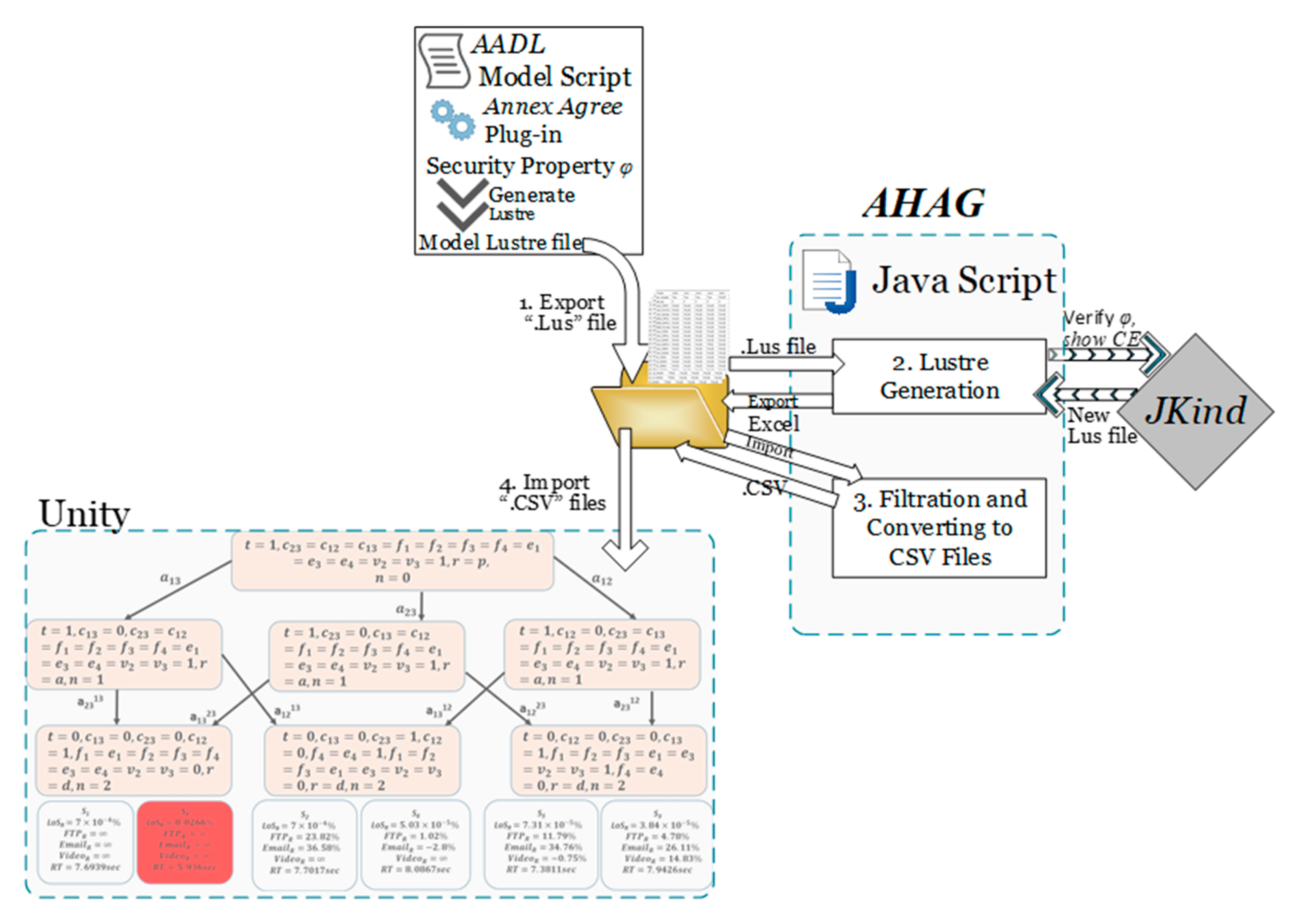
Processes | Free Full-Text | Automatic Hybrid Attack Graph (AHAG) Generation for Complex Engineering Systems

Hybrid unsupervised web-attack detection and classification – A deep learning approach - ScienceDirect
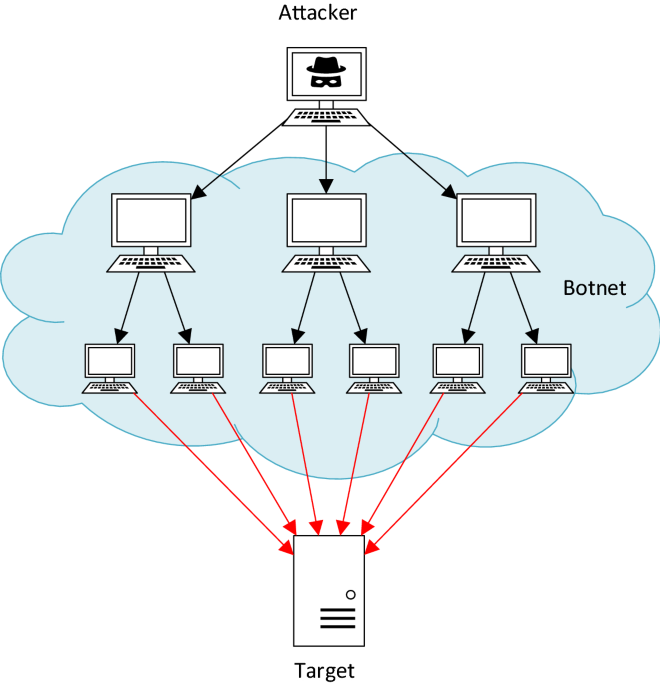
A hybrid machine learning approach for detecting unprecedented DDoS attacks | The Journal of Supercomputing

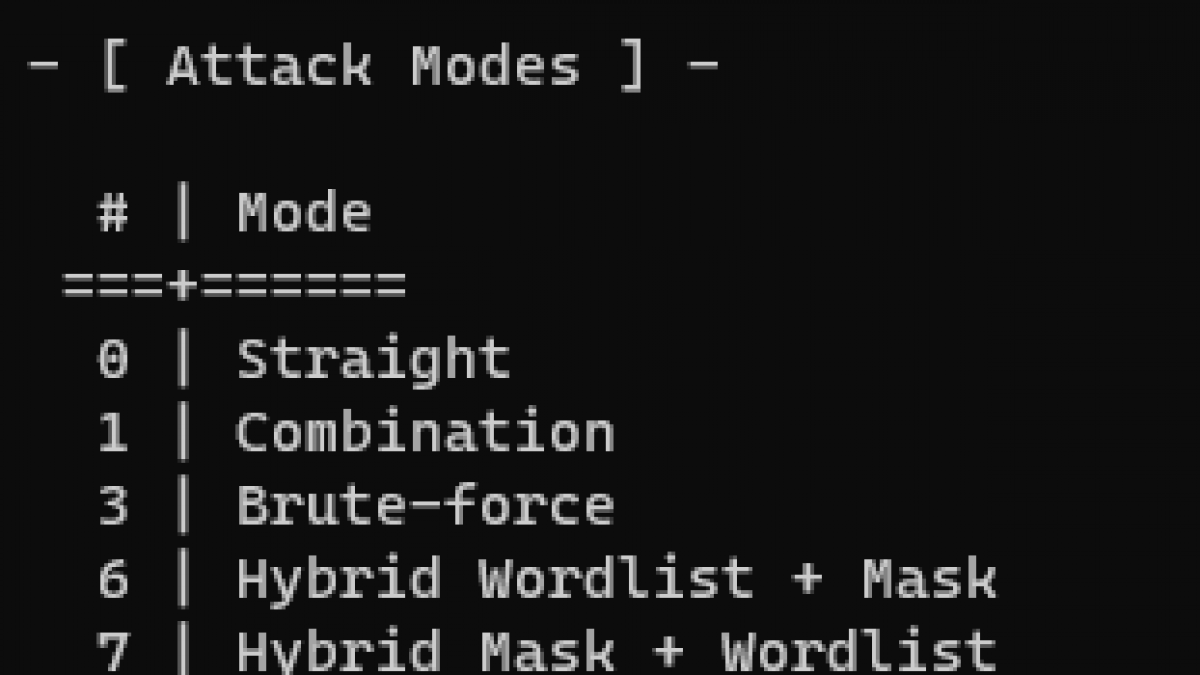


![ALERT] There Is A New Hybrid Cyber Attack On Banks And Credit Unions In The Wild ALERT] There Is A New Hybrid Cyber Attack On Banks And Credit Unions In The Wild](https://blog.knowbe4.com/hubfs/hybrid_attack.png)